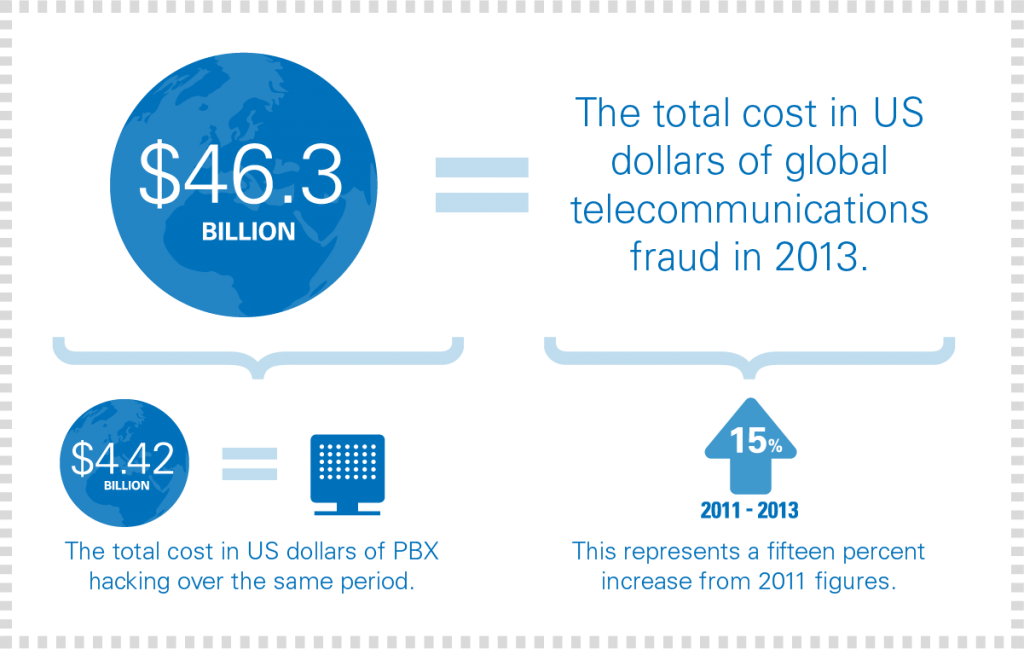
How Do People make Money from Toll Fraud?
Like all technological scams, people commit toll fraud because it is a brilliantly irritating combination of anonymity, profitability, and scalability. While there are as many different variations in approach as there are companies to exploit, primarily the scams that we see getting run use one of the following methods.
Phone Cards

In the first instance the person will sell phone cards with heavily discounted international call rates. When a consumer uses the card, their call is connected to the international destination via an unsuspecting company’s PBX. Eventually the company will be hit with a massive bill for outgoing calls, rectify the security flaw, and the scammer will simply move on to the next unsuspecting victim. Because the scammer has passed off his primary cost structure, any money gained from the sale of the cards is money in the bank.
Premium Rate Numbers

The second scam is conceptually much simpler because requires neither phone cards nor an unsuspecting third party. Once the scammer has control of a company’s PBX they places a series of calls to premium rate numbers that he/she owns (the kind people would ordinarily call to talk to a very special person for $12.99 a minute). But unlike your typical premium rate number, there is no special person at the other end, just a voice recording inanely muttering in order to maintain the verisimilitude of a conversation. This is done to minimise the chances that the call is flagged as fraudulent and dropped. Meanwhile the charges pile up, and the scammer pockets the proceeds.
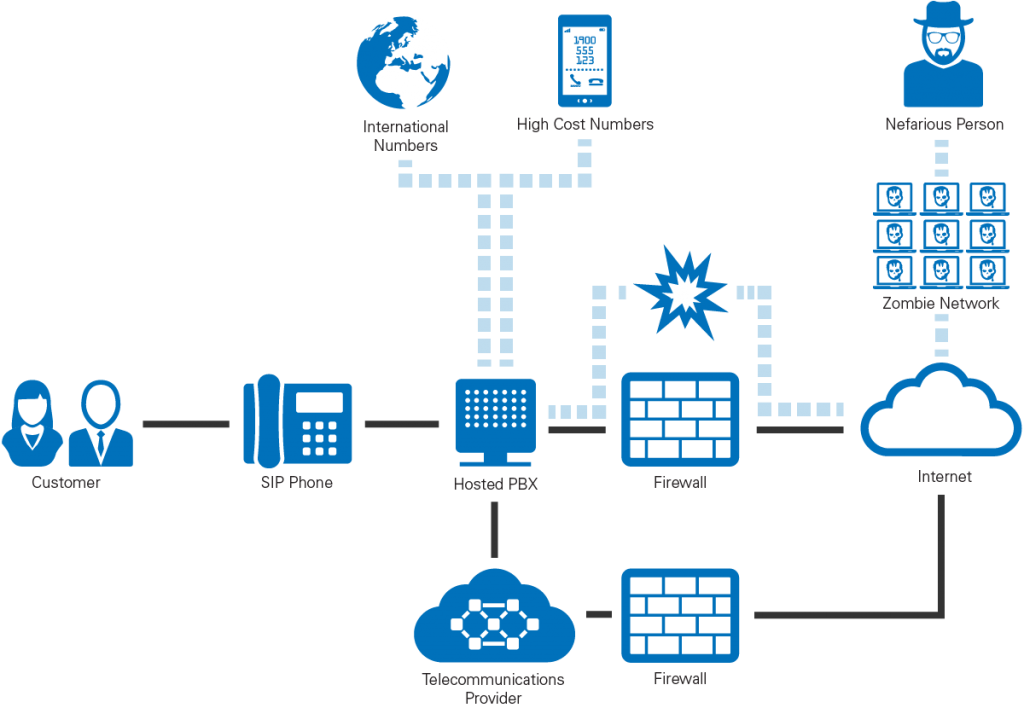
How do scammers get access to a PBX?
There are many different types of toll fraud and we won’t be going into all of them today. Instead we are going to focus on the one we see as being the most pertinent to Australian businesses: PBX hacking. Typically a scammer will write a script that crawls the internet looking for vulnerabilities in companys’ firewalls (like open ports). Once an opening is detected, the scammer can then punch requests at it in order to tease out information about what the system is and how it might be vulnerable. Eventually they will have all the information they need to brute force their way through the firewall. For anonymity purposes and to reduce their own infrastructure costs, experienced scammers will do this via either a proxy, or a botnet (sometimes called a zombie network) of previously hacked computers.
Once the firewall has been breached the scammer can gain access to the PBX, build a back door into the system, and use it to route as much traffic through it as they think they can get away with.
What do Telco’s do to protect against it
From the Telco’s perspective (assuming it has been done elegantly) toll fraud is very difficult to detect. This is due to the fact that the traffic appears to be authentically originating from the company’s PBX with the source IP, user account, user ID, and password all matching the company’s records.
This means that some of the best tools in a telecommunications provider’s arsenal are the ability to monitor for the presence of toll fraud by scanning for atypical call activity, and the imposition of limitations to minimise the damage that can be done. For security reasons we will refrain from going into specifics, but the following list represents some typical strategies that providers employ:
Imposing channel limitations
Along with bandwidth limitations, toll fraud is one of the primary reasons that providers limit the number of concurrent calls that can be made from a single PBX. While this tactic may not actively discourage fraudsters, it limits the amount of damage that can be done over a short space of time. Because providers can see the number of calls that are attempting to connect (not just the ones that get put through) they are able to use this as an indicator of abnormal traffic activity. Additionally, because the vast majority of call fraud occurs to international numbers (see the picture below), providers will often impose separate limitations on how many concurrent international calls a customer can make.
Imposing a threshold on the maximum per minute cost of a phone call
Providers often impose an upper limit on the per-minute costs of calls that they are happy to connect, unless clients have specifically request that this limitation be removed. This limitation is used to prevent scammers from being able to dial premium rate numbers, such as 1900 numbers.
Limiting the amount of credit that a company is extended
In a worst case scenario, telecommunications providers seek to protect their customers from exorbitant call costs by placing an upper threshold on the amount of billable calls that a company is able to incur. The rules around this differ from provider to provider, and are likely to be dependent on the size of a company’s average bill, so it is worth checking with your provider what your limit is and negotiating an increase or decrease as you see fit.
What can you do to protect against PBX Hacking?
Use complex and varied passwords
Time and time again we find toll fraud comes back to weak passwords. So even though it seems obvious, we are going to say it anyway: “Don’t use common passwords like 1234, password, guest, 1000, test, or the same four digit code as the extension phone”. If you have trouble remembering your passwords, either use some secure software like Keepass to generate and keep track of them, or use a combinations that are easy to remember like “14CharlieSheen?” or “3BlindMice!”.
Check your ISDN failover configuration
If you are using SIP based telephony, but have also chosen to maintain or setup a failover to an ISDN line, make sure your ISDN lines can’t be used to call high toll numbers. Why? Because if a scammer bombards your PBX with traffic, it is likely that some of the fraudulent calls, being unable to connect via SIP, will fail-over to the much more expensive ISDN connection.
Block country prefixes
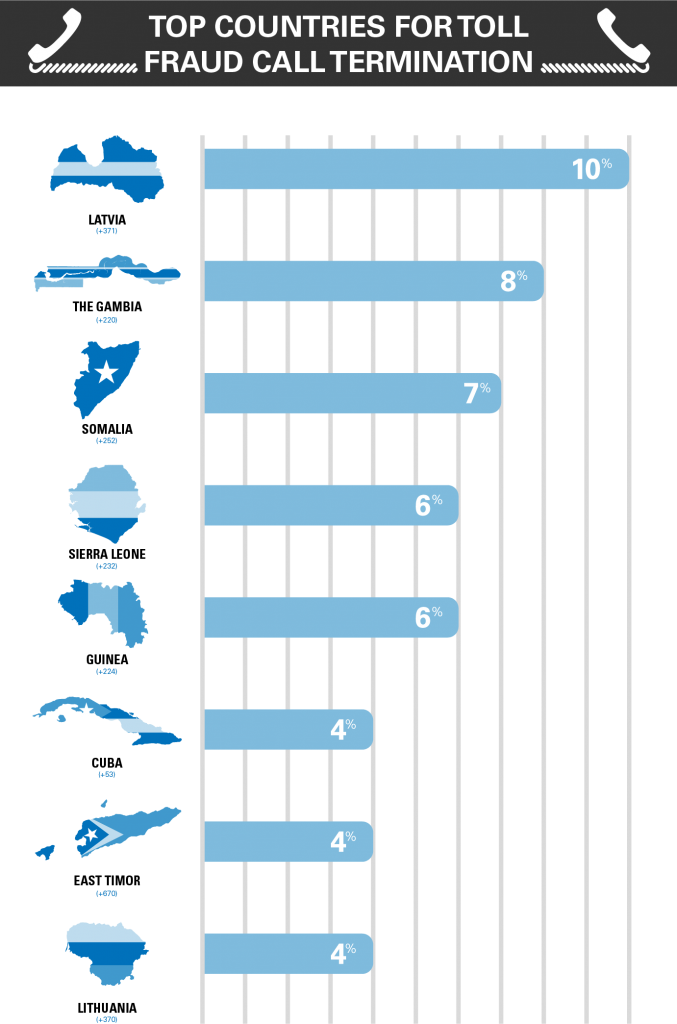
Most PBX’s allow customers to block outbound traffic to international numbers. So if you only conduct business domestically this is one of the best options available. Not only does it impose additional limitations on hackers, it is capable of preventing other less technologically advanced forms of toll fraud (such as late night staff making long calls to family members in other countries). Even if your business frequently needs to call international numbers, it is still unlikely that it will need to call all of them. As such, we recommended that you block all unnecessary destinations. Unless you have a clients or suppliers in these countries, this list of the top destinations for toll fraud call terminations might be a good place to start.
If your Telco also provides your WAN make sure you ask for a managed firewall
Telecommunications providers have a lot more experience with toll fraud than your average IT manager, and have become much more adept at configuring firewalls so as to minimise the chances of a breach as a result. If this option is available to you, we would suggest that you take advantage of it as it is going to make things a lot harder for the scammer.
Minimise the visibility of your PBX to the web.
If you are choosing to manage your own firewalls, wherever possible avoid leaving open ports available for staff to remotely access your PBX. Remember this is how most scammers are able to hack in, so avoid doing it unless it is absolutely necessary.
These are just a few of the techniques available and this list is far from all encompassing, but as with most technological scams, even implementing basic security measures makes a huge difference to how likely you are to be targeted. However, if you are interested in a more comprehensive solution, we would recommend talking to your telecommunications provider about what options they have available, and what they recommend for your organisation.

